South Dakota Election Myths vs Facts
Click on the Question to see the answer. Click again to hide.
FACT: This is a false claim. Here’s what we are doing:
- SD implements voter photo ID on in-person and absentee voting
- SD uses paper ballots
- Local election offices have security and detection measures in place that make it highly difficult to commit fraud through counterfeit ballots. While the specific measures vary, in accordance with state and local election laws and practices, ballot security measures can include signature matching, information checks, barcodes, watermarks, and precise paper weights.
- Tabulating equipment is NOT connected to the internet
- Tabulators are not connected to any network. The tabulators DO NOT have any wired data connections, no wireless connections, there are no modems in SD tabulators. Tabulators are not connected to any county network or the Internet. They are an isolated piece of technology.
- SD doesn’t allow for ballot drop boxes
- SD has built relationships with local, state and federal partners to ensure that elections are run securely
- Safeguards and security are built into processes.
- SD has recently passed post-election audit legislation for primay and general elections. The post-election audit process will thoroughly review procedures performed before, during, and after an election. The review of voted ballots will verify the equipment used to count votes worked properly and yielded the correct results.
- Poll watchers are encouraged to participate in elections and are an integral part of the voting process.
FACT: No. South Dakota law prohibits tabulating machines from being connected to the internet. As noted in the statute below, South Dakota Codified Law (SDCL) 12-17B-2 states that no automatic tabulating or electronic ballot marking devices may be connected to the internet. Furthermore, the tabulation machines used in South Dakota counties do not contain modems and are incapable of being connected to the internet. Similarly, the ballot marking device used in South Dakota counties is a hardened ballot-marking device that does not contain a modem and is incapable of being connected to the internet. It is an isolated piece of technology. Every vote tabulator is stored securely when not in use.
12-17B-2. Requirements for automatic tabulating, electronic ballot marking, and election voting equipment systems--Approval of changes or modifications.Any automatic tabulating or electronic ballot marking system used in an election shall enable the voter to cast a vote for all offices and on all measures on which the voter is entitled to vote. No automatic tabulating, electronic ballot marking, or election voting equipment system may be connected to the internet. No ballot marking device may save or tabulate votes marked on any system. Each system shall fulfill the requirements for election assistance commission standards certification and be approved by the State Board of Elections prior to distribution and use in this state. No system may be approved unless the system fulfills the requirements as established by the State Board of Elections. Any changes or modifications to an approved system shall be approved by the State Board of Elections prior to distribution and use.
FACT: Every county tabulator undergoes a logic accuracy test (basically a pre-election audit) in which the public is invited to attend and watch. Sample ballots are tested on the machine to ensure the tabulators are working correctly and recording votes properly. Post-election audits will be conducted in all counties in South Dakota for primary and general elections to ensure the hand-count and tabulator totals match. Additionally, South Dakota has conducted numerous recounts in several counties in recent years, again verifying the accuracy of the vote tabulators.
Again, there is no network connectivity with a tabulator.
FACT: County auditors regularly update their voter registration lists based on voter requests and data from varying sources that may indicate that a voter has died, moved, registered elsewhere, changed their name, or become otherwise ineligible. These data sources include South Dakota Department of Public Service Motor Vehicle (drivers licensing), vital records, confirmation notices mailed to voters, and unified judicial system. This helps election officials identify and merge duplicate records, and remove records for individuals who are no longer eligible.
FACT: State and federal laws prohibit voter impersonation, including voting on behalf of an individual who has died, moved, or otherwise become ineligible yet whose record remains temporarily on the voter rolls. Additional election integrity safeguards, including signature matching and verification of other personal data, protect against people casting ballots on behalf of others. Removal of deceased individuals is based on death records shared by state vital statistics agencies and the Social Security Administration. While there can be lag time between a person’s death and their removal from the voter registration list, which can lead to some official election mail, including mail-in ballots being delivered to addresses of deceased individuals, death records provide a strong audit trail to identify any attempts to cast ballots on behalf of deceased individuals. Additional election integrity safeguards, including signature matching and information checks, further protect against voter impersonation and voting by ineligible persons. In some instances, living persons may return mail-in ballots or vote early in-person, and then die before Election Day. Some states permit such voters’ ballots to be counted, while others disallow such ballots and follow procedures to identify and reject them during processing. South Dakota does not count these ballots.
Taken out of context, some voter registration information may appear to suggest suspicious activity, but is actually the result of an innocuous clerical error or intended data practices. For example, in rare instances when a registrant’s birth date is not known (e.g., a voter who legally registered prior to modern voter registration practices), election officials may use temporary placeholder data (e.g., 1/1/1900) until the registrant’s birth date can be updated. In other instances, a voting-age child with the same name and address as their deceased parent could be misinterpreted as a deceased voter or contribute to clerical errors.
FACT: Election officials utilize various security measures to protect the integrity of the mail-in/absentee voting process.
- Only registered South Dakota voters are eligible to vote absentee-by-mail.
- Voters must complete and sign an application for an absentee ballot and mail the original signed application to their county auditor. The application must also be notarized or include a copy of their photo ID, which both serve to verify the identity of the applicant.
- Upon verification of registered status and completed application by county auditor, the voter will be mailed an absentee ballot packet.
- The voter will mark the ballot and place the voted ballot in the enclosed return envelope. The voter will then sign their name on the reverse side of the return envelope (to be verified against the signature on the absentee application).
- Upon receipt of the returned absentee ballot envelope, the county auditor places the envelope in a secure area in their office and notates a returned ballot for the voter within the statewide voter registration list. This step prevents a voter from returning an absentee ballot and voting on election day.
- The absentee ballot envelopes are not opened until election day. The absentee ballots will be processed at polling places corresponding to the voter’s precinct or by an absentee precinct board located in the same building as the county auditor’s office.
- When processing the absentee ballots, the voter’s name will be verified in the statewide voter registration list. The voter’s signature on the absentee ballot application is compared to the voter’s signature on the reverse side of the absentee ballot return envelope to make sure they match. Upon confirmation of matching signatures, the voter’s name will be written in the pollbook.
- Absentee ballots are removed from envelopes without unfolding the ballot and the official ballot stamp is applied to the ballot. The ballots are then placed in a secure ballot box to be tabulated with the rest of the ballots.
- No results are printed or displayed until all polling places have closed in the state.
- Election day processes are open to the public to observe.
FACT: State and local election officials implement varying testing practices to help ensure voting system software function as intended. These practices include federal and state testing and certification, testing prior to procurement, acceptance testing, and/or pre- and post-election logic and accuracy testing. Such testing helps detect and protect against malicious or anomalous software issues. County officials compare all vote totals shown on the Internet with their own totals to ensure they match up.
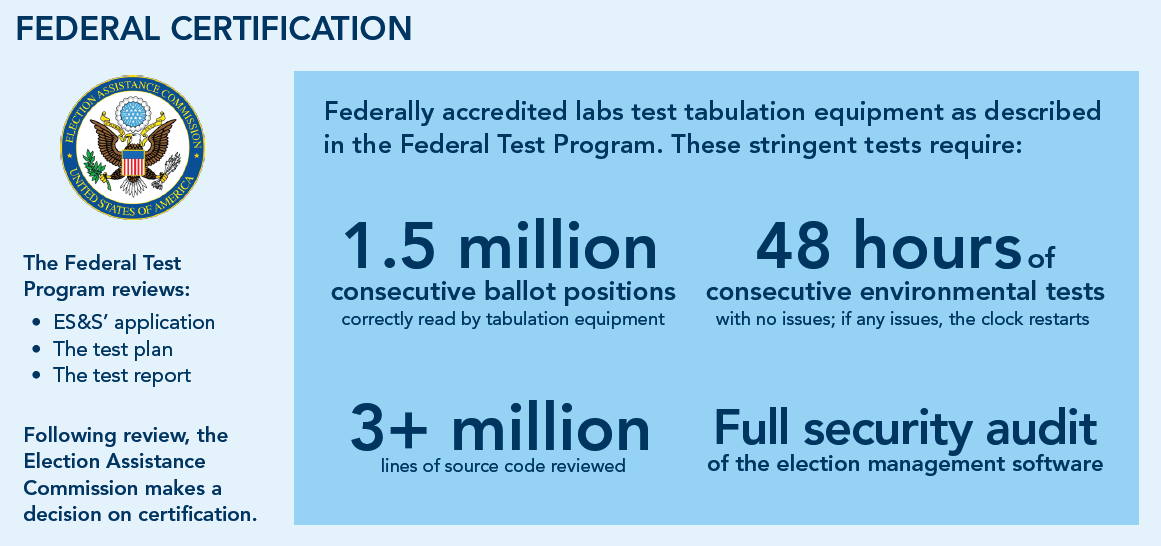
All ES&S tabulation systems are submitted to rigorous and extensive independent test campaigns as part of the (EAC) Voting System Certification Program. The EAC’s security performance standards, developed by scientists, academicians, and election officials, ensure unrivaled security.
Here’s a little snippet about the federal certification the machines have to pass.
FACT: Election results are not final until certification. Election night reporting is unofficial and those results may change as ballot counting is completed. Election results reported on election night are always unofficial and are provided solely for voters’ convenience. In fact, no state requires that official results be certified on election night itself. Fluctuations in unofficial results reporting will occur during and after election night as more ballots are processed and counted, often including military and overseas ballots, and validated provisional ballots. Variations in state processes may also mean ballots cast through different methods (e.g., early in-person voting, mail-in voting, and election day voting) are counted and unofficially reported in different orders. There may also be recounts across South Dakota that could change results. Official results are released after rigorous canvassing (verification) and certification by local and state election officials. South Dakota's are considered FINAL after the state canvass.
FACT: Some voter registration information is public information and is available to political campaigns, researchers, and often members of the public, frequently for purchase.
A few years ago, our office worked to take the full date of birth off the voter file to help protect voter information.
12-4-9. Master registration file--Contents--Public inspection--Limitations.
The county auditor shall maintain and safeguard a file of voters in computer format that contains the information of each person registered in each voting precinct within the county. This file shall be known as the master registration file and shall be, at all times during office hours, open to public inspection. However, public access to social security numbers, driver license numbers, and dates of birth contained in the master registration file is prohibited. The master registration file shall contain all information from each voter's registration card. The master registration file shall also include the date of the last election the voter has voted in and when the voter's information was last updated. The master registration file may also contain additional voter history information. Any voter registration form for a purged or unregistered voter shall be kept for twenty-two months. No purged or unregistered voter may be included in the master registration file.
FACT: South Dakota DOES NOT have online registration. Websites can experience outages for non-malicious reasons. Outages occur for a variety of reasons, including configuration errors, hardware issues, natural disasters and communications infrastructure issues.
FACT: Elections are administered at the local level by duly elected County Auditors, their staff and locally trained individuals. Local officials establish local polling locations, employ local workers to staff the polls, test and verify equipment in their office, count votes, submit vote totals, and work extremely hard to ensure that elections go off without a hitch. State officials assist in establishing laws, training, regulations and certifications. Federal officials offer intelligence on a voluntary basis regarding cybersecurity and physical security.
DHS and CISA operate in support of state and local election officials, and do not administer elections or handle ballots. CISA’s role in election security includes sharing information, such as cyber threat indicators, with state and local election officials, as well as providing technical cybersecurity services (e.g., vulnerability scanning) upon the request of those officials.
FACT: Hacks of state and local IT systems should not be downplayed; however, a compromise of state or local IT systems does not mean those systems are election-related. Even if an election-related system is compromised, a compromise of a system does not necessarily mean the integrity of the vote has been affected. Election officials have multiple safeguards and contingencies in place, including provisional ballots or backup paper poll books that limit the impact from a cyber incident with minimal disruption to voting. Additionally, having an auditable paper record ensures that the vote count can be verified and validated.
FACT: Safeguards are in place to prevent home-printed or photocopied mail-in ballots from being counted. Committing fraud through photocopied or home-printed ballots would be highly difficult to do successfully and is ILLEGAL. This is because each local election office has security measures in place to detect such malicious activity. Such security measures include signature matching, information checks, and barcodes. Paper ballots are ran through tabulating machines and would kick out any ballots that were fraudulently made.
FACT: Like all systems, tabulators can malfunction. Similarly, properly functioning tabulator may be unable to scan ballots that are damaged, misprinted, or have ambiguous markings. When a ballot cannot be read by a tabulator, election officials apply procedures to securely store the ballots until they can be counted at a later time. Because the paper ballot itself is the official record of the votes, there is no impact on the accuracy or integrity of election results.
FACT: Variations in vote totals for different contests on the same ballot occur in every election and do not by themselves indicate fraud or issues with voting technology. Variations in vote totals for different contests on the same ballot occur in every election. For example, this can occur as a result of “undervotes.” An undervote occurs when the number of choices selected by a voter in a contest is less than the maximum number allowed for that contest or when no selection is made for a single choice contest. These variations by themselves are not indications of issues with voting technology or the integrity of election processes or results.
FACT: The systems and processes used by election officials to tabulate votes and certify official results are protected by various safeguards that help ensure the accuracy of election results. These safeguards include measures that help ensure tabulation systems function as intended, protect against malicious software, and enable the identification and correction of any irregularities.

